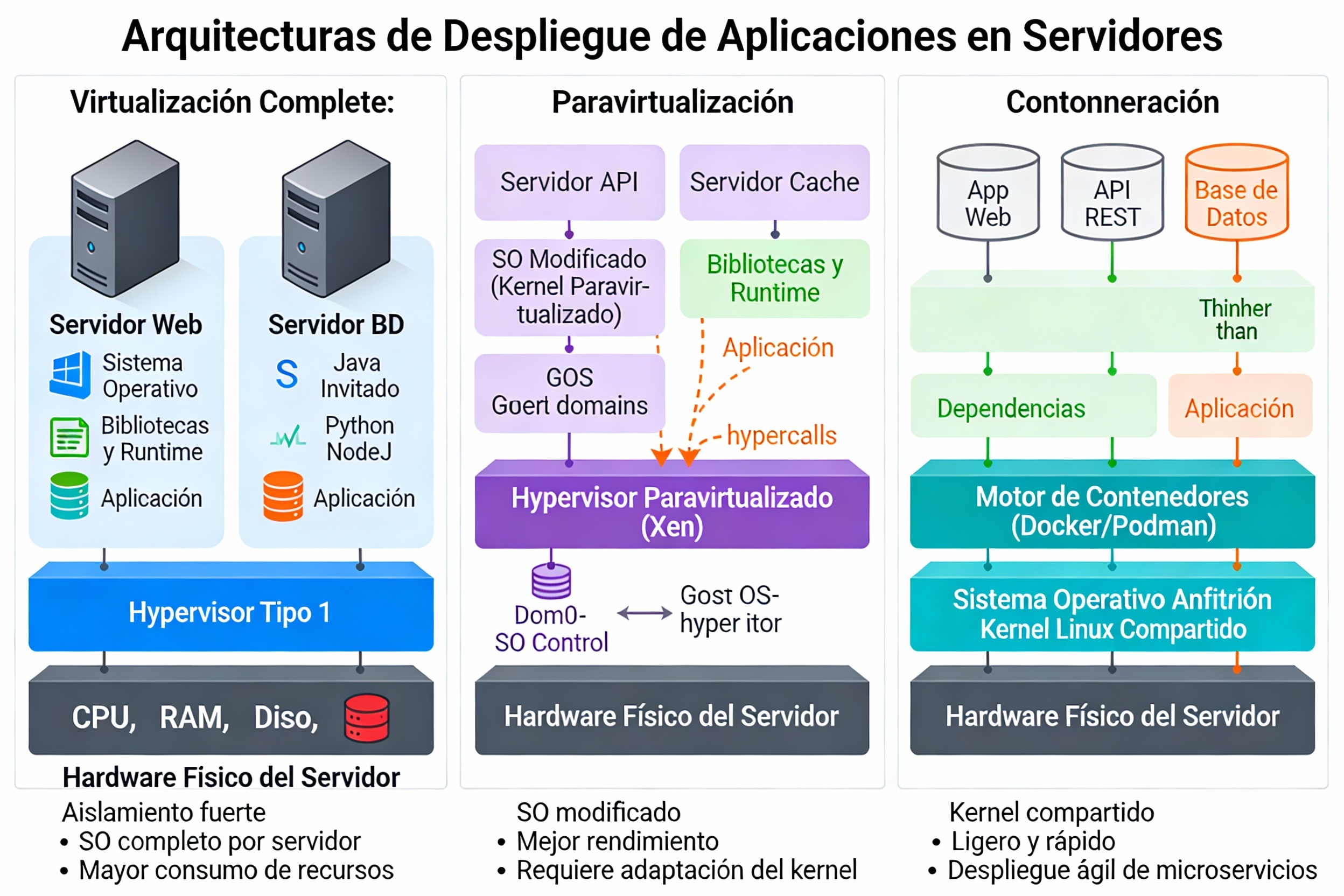
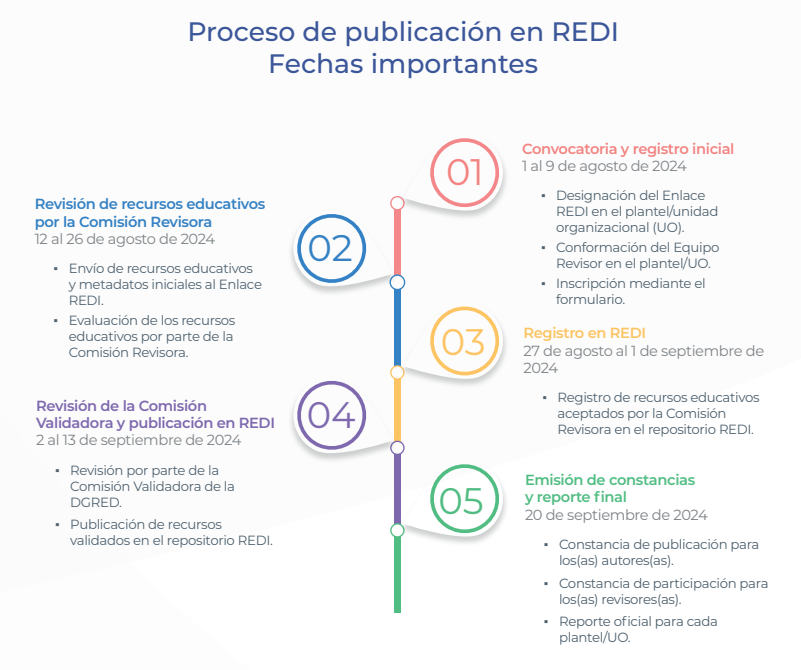
Referencias consultadas:
REFERENCIAS BIBLIOGRÁFICAS
Libros y Documentación Técnica
M. Portnoy, Virtualization Essentials, 2nd ed. Indianapolis, IN: Sybex, 2016.
J. Turnbull, The Docker Book: Containerization is the New Virtualization. USA: James Turnbull, 2014.
K. Hess and A. Newman, Practical Virtualization Solutions: Virtualization from the Trenches. Upper Saddle River, NJ: Prentice Hall, 2010.
D. Merkel, "Docker: Lightweight Linux Containers for Consistent Development and Deployment," Linux Journal, vol. 2014, no. 239, 2014.
S. Soltesz et al., "Container-based Operating System Virtualization: A Scalable, High-performance Alternative to Hypervisors," in Proceedings of the 2nd ACM SIGOPS/EuroSys European Conference on Computer Systems, 2007, pp. 275–287.
Cloud Computing y Servicios
P. Mell and T. Grance, "The NIST Definition of Cloud Computing," National Institute of Standards and Technology, Special Publication 800-145, 2011. [Online]. Available: https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-145.pdf
R. Buyya, C. S. Yeo, S. Venugopal, J. Broberg, and I. Brandic, "Cloud Computing and Emerging IT Platforms: Vision, Hype, and Reality for Delivering Computing as the 5th Utility," Future Generation Computer Systems, vol. 25, no. 6, pp. 599–616, Jun. 2009.
L. M. Vaquero, L. Rodero-Merino, J. Caceres, and M. Lindner, "A Break in the Clouds: Towards a Cloud Definition," ACM SIGCOMM Computer Communication Review, vol. 39, no. 1, pp. 50–55, Jan. 2009.
Virtualización: Hypervisores y Tecnologías
P. Barham et al., "Xen and the Art of Virtualization," in Proceedings of the 19th ACM Symposium on Operating Systems Principles (SOSP '03), Bolton Landing, NY, 2003, pp. 164–177.
A. Kivity, Y. Kamay, D. Laor, U. Lublin, and A. Liguori, "KVM: the Linux Virtual Machine Monitor," in Proceedings of the Linux Symposium, vol. 1, Ottawa, Canada, 2007, pp. 225–230.
J. Sugerman, G. Venkitachalam, and B.-H. Lim, "Virtualizing I/O Devices on VMware Workstation's Hosted Virtual Machine Monitor," in Proceedings of the 2001 USENIX Annual Technical Conference, Boston, MA, 2001, pp. 1–14.
G. J. Popek and R. P. Goldberg, "Formal Requirements for Virtualizable Third Generation Architectures," Communications of the ACM, vol. 17, no. 7, pp. 412–421, Jul. 1974.
Contenedores: LXC, LXD, Docker
"LXC - Linux Containers," Canonical Ltd. [Online]. Available: https://linuxcontainers.org/lxc/introduction/
"LXD - System Container Manager," Canonical Ltd. [Online]. Available: https://linuxcontainers.org/lxd/introduction/
Docker Inc., "Docker Documentation," 2024. [Online]. Available: https://docs.docker.com/
W. Felter, A. Ferreira, R. Rajamony, and J. Rubio, "An Updated Performance Comparison of Virtual Machines and Linux Containers," in 2015 IEEE International Symposium on Performance Analysis of Systems and Software (ISPASS), Philadelphia, PA, 2015, pp. 171–172.
R. Morabito, J. Kjällman, and M. Komu, "Hypervisors vs. Lightweight Virtualization: A Performance Comparison," in 2015 IEEE International Conference on Cloud Engineering, Tempe, AZ, 2015, pp. 386–393.
Seguridad y SSH
T. Ylonen and C. Lonvick, "The Secure Shell (SSH) Protocol Architecture," RFC 4251, Internet Engineering Task Force (IETF), Jan. 2006. [Online]. Available: https://www.rfc-editor.org/rfc/rfc4251
T. Ylonen and C. Lonvick, "The Secure Shell (SSH) Authentication Protocol," RFC 4252, IETF, Jan. 2006. [Online]. Available: https://www.rfc-editor.org/rfc/rfc4252
M. Friedl, N. Provos, and W. Simpson, "Diffie-Hellman Group Exchange for the Secure Shell (SSH) Transport Layer Protocol," RFC 4419, IETF, Mar. 2006.
D. J. Barrett, R. E. Silverman, and R. G. Byrnes, SSH, The Secure Shell: The Definitive Guide, 2nd ed. Sebastopol, CA: O'Reilly Media, 2005.
Redes y BGP
Y. Rekhter, T. Li, and S. Hares, "A Border Gateway Protocol 4 (BGP-4)," RFC 4271, IETF, Jan. 2006. [Online]. Available: https://www.rfc-editor.org/rfc/rfc4271
J. Stewart, BGP4: Inter-Domain Routing in the Internet. Reading, MA: Addison-Wesley, 1999.
G. Huston, "BGP Routing Table Analysis Reports," CIDR Report. [Online]. Available: https://www.cidr-report.org/
Criptografía
W. Stallings, Cryptography and Network Security: Principles and Practice, 8th ed. Harlow, UK: Pearson Education, 2020.
B. Schneier, Applied Cryptography: Protocols, Algorithms, and Source Code in C, 2nd ed. New York: John Wiley & Sons, 1996.
National Institute of Standards and Technology (NIST), "Advanced Encryption Standard (AES)," FIPS PUB 197, Nov. 2001.
Recursos en Línea
"KVM - Kernel Virtual Machine," Red Hat Inc. [Online]. Available: https://www.linux-kvm.org/
"Understanding Linux Containers," Red Hat Developer. [Online]. Available: https://developers.redhat.com/blog/2018/02/22/container-terminology-practical-introduction
"LXDWARE - Web-based GUI for LXD," GitHub. [Online]. Available: https://github.com/lxdware/lxd-dashboard